How Buddler works with your data
This page provides answers to the key questions about the data Buddler uses and how it is stored, processed, and protected. We implement modern technical and organizational security measures, which may be updated from time to time, but always maintain a high level of data protection.
- What is your data the Buddler works with
- User sign-up and log in
- Mandatory registration conditions at Buddler
- Possible errors during registration or authorization
- Requesting sensitive data areas using OAuth 2.0
- Justification for the requested scope of the Google Search Console API
- Keeping Data Up to Date in Buddler
- Access to User’s Account
- Data Retention Period and Deletion
- Technical security measures for the project
- GDPR
What is your data the Buddler works with
User sign-up and log in
In our app, Google authorization is the only possible method of registration and authorization for the following reasons.
- When authorizing through Google, users can be confident that only they will have access. There’s no need to generate or remember a separate log in or password; the app doesn’t need to store or process this sensitive information.
- Google Search Console accounts are connected to Gmail, making it convenient to request access within the authorization window when users log in or after signing up for their account.
Mandatory registration conditions at Buddler
Acceptance of the terms, available through the relevant links on the registration form, is mandatory to register in Buddler.
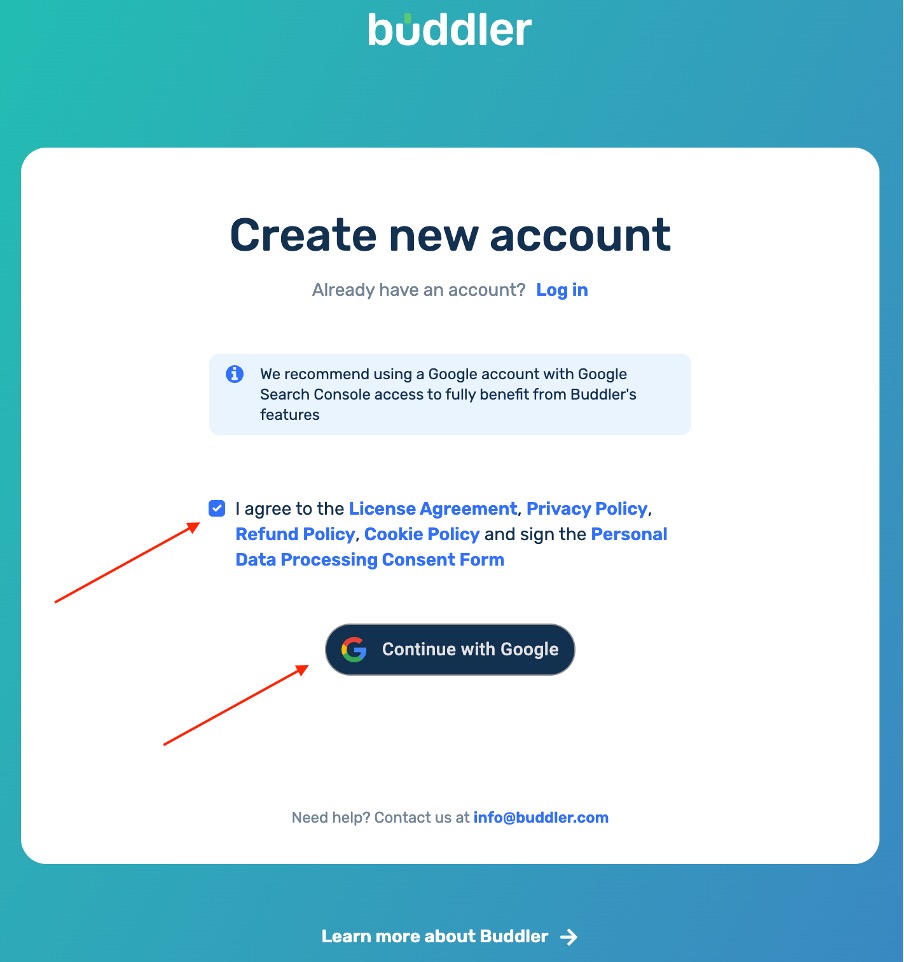
Possible errors during registration or authorization
In case of registration or authorization through internal meta browsers or other internal browsers of some social networks or applications used on mobile devices, OAuth 2.0 may generate an error. Registration or authorization will fail in this case.
It is not a bug in our application, it is a conflict between the internal browser and Google OAuth 2.0. Considering the device, its operating system version and internal device settings, such conflicts occur only for some users.
In this case, we suggest using a buddler.com site transition in Chrome or Safari to avoid conflicts with OAuth 2.0.
Requesting sensitive data areas using OAuth 2.0
To ensure that our web application delivers the necessary research results to users, we must collect data from the Google Search Console for processing. This data is obtained from websites that are both accessible and relevant to the user’s interests.
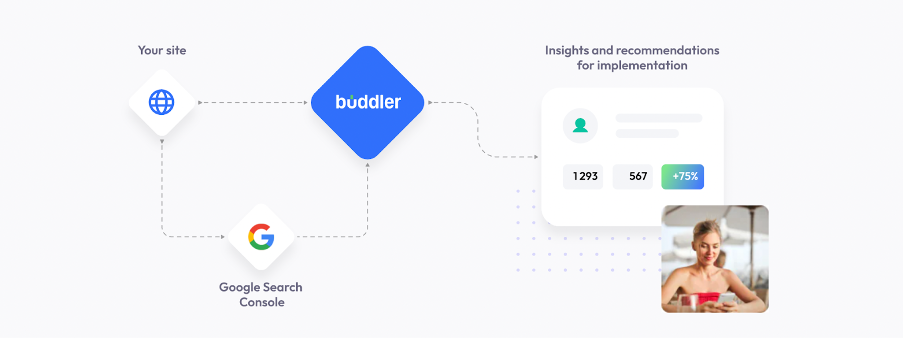
To gather data, user authentication through Google is essential. This involves requesting permission to access the user’s Google Search Console account, associated with their Gmail through Google authorization.
As a result, our web application uses several areas containing confidential and sensitive data.
- Google Sign-In, Scopes: email, OpenID, profile
- Google Search Console API, v1, Scopes: View Search Console data for your verified sites
Justification for the requested scope of the Google Search Console API
During the Google authorization, the application requests access to the Google Search Console API, v1 Scope: View Search Console data for your verified sites.
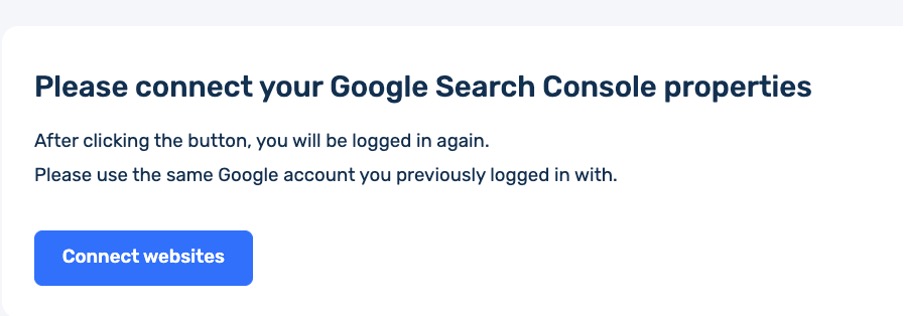
This is the minimum scope required for the Google Search Console API, because the application does not affect the user’s data. It collects data through queries and performs calculations on its side, with the results reflected in reports within the user’s personal account interface in our app. During registration, granting permissions for this scope is not mandatory and can be done after registration and agreement acceptance within the personal account by clicking the ‘Connect websites’ button.
This button brings up the OAuth 2.0 window and allows you to select the desired Google Account to grant access to. When you grant access to Buddler, all currently available GSC properties in the selected account will be displayed.
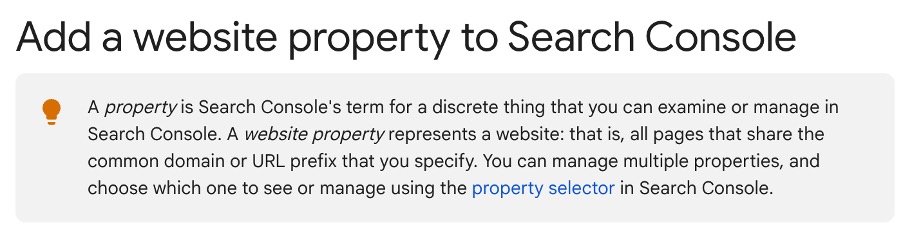
Buddler supports all the same types of properties that Search Console has:
- URL-prefix property (https://example.com)
- Domain property (example.com)
- Google-hosted property (Sites, Blogger, Workspace)
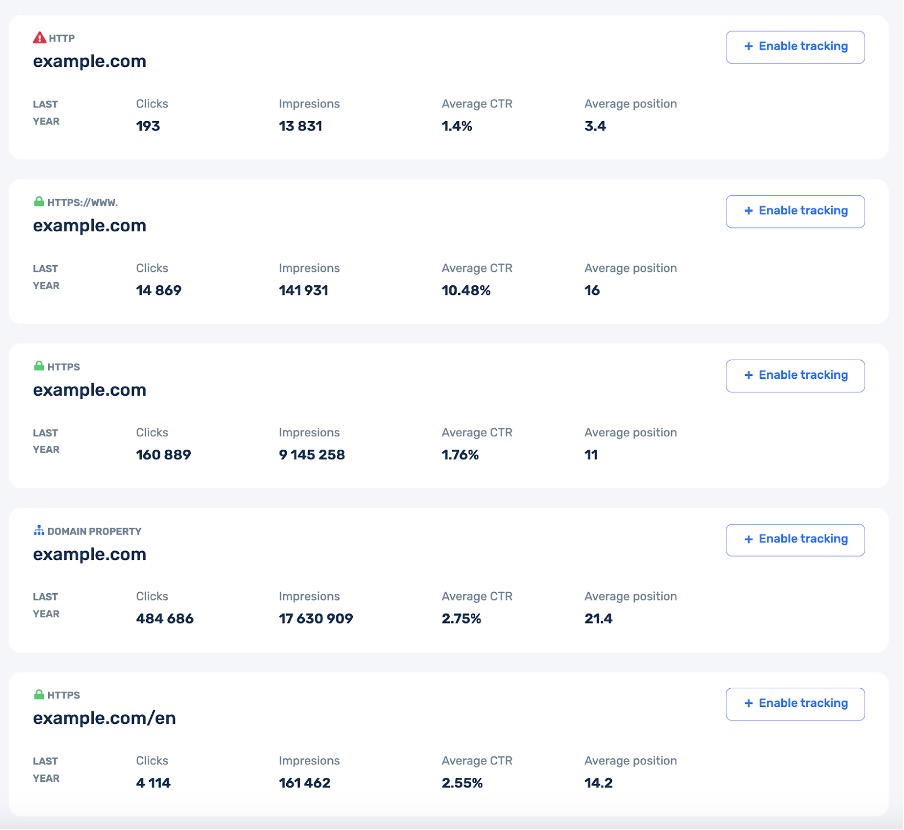
Example of displaying the list of properties in the SEO Performance Monitor section.
You can connect sites (give access to read GSC API data) to another Gmail account available to you that does not match the one you registered for.
It is done to allow you to receive notifications from the system at your preferred email address, without being strictly tied to the email associated with your GSC account. However, at this time, only one GSC account can be connected, meaning 1 GSC account = 1 Buddler account.
If you have already granted access to an account during registration, this button will not be displayed for you.
Keeping Data Up to Date in Buddler
Each time a user logs into their personal account, we check whether Buddler has access to Google Search Console (GSC) and verify the list of available properties to maintain an up-to-date list for analysis or monitoring. If a property that was previously available is no longer accessible, we will not be able to collect or process data for it, and this change will be reflected in your account.
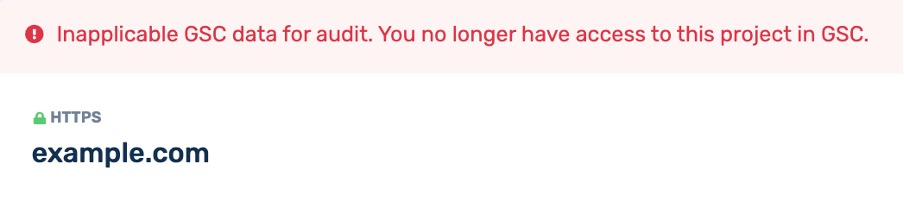
Example of how a previously available property appears in the SEO Analytics Reports section after losing access to GSC.
Data and report results will be stored for these properties in accordance with the general terms of use of Buddler or the individual terms outlined in the agreement between the parties for the Enterprise.
We also use offline updates for GSC access tokens, which allows Buddler to collect properties daily, check the relevance of data for the past 3 days, and replace temporary GSC data with final values added to the SEO Performance Monitor.
For Enterprise customers, we offer GSC + BigQuery integration or connection to any other databases used by the user to store data obtained via BigQuery from GSC.
Since connecting BigQuery to GSC is only possible for GSC owners, we do not request owner-level access or configure it on our end. Instead, we provide guidance and consultations to help with the setup. Once data collection in BigQuery is configured—or if the user is already collecting data there—we assess storage and processing volumes, make a commercial offer, and suggest data transfer options to Buddler.
Since BigQuery does not only charge you for the data storage but also for operations, keeping data in Buddler is more cost-effective, as we do not charge for operations. Based on the volume of data, selected data transfer methods to Buddler, and any additional customized options, an offer is calculated, and a contract is drawn up with the support of an international lawyer. Based on this, we provide the software and organize data storage according to the selected pricing plans.
Access to User’s Account
Since Buddler registration and authorization are only possible through Google, access to the personal account and Buddler reports is unavailable to other Buddler users and is only available to the owner of the Gmail account linked to GSC.
In case you give someone access to your Gmail account, those people will also be able to use your Buddler account, since authorization is regulated via OAuth 2.0.
If several accounts have access to the same property (e.g. the owner gave access to a contractor), both of these people will be able to register separately from each other in Buddler and use their own reports and monitoring without overlapping with other accounts.
Data Retention Period and Deletion
After the trial ends and without extending the paid plan, your RAW (original) data will be stored for free for 60 days.
Previews not redeemed for credits in the SEO Analytics Reports are stored in the audit history and remain available for 90 days. You can open the preview as many times as you like, and you can redeem it within 90 days after the audit is ready. However, we recommend redeeming fresh audits, as they contain the most up-to-date data.
Sites added for monitoring will stop collecting data within the SEO Performance Monitor and will no longer upload data in the background daily. Free storage of already collected raw data will also be available for 60 days.
If the user does not want to continue transmitting data to the application, it is sufficient to revoke the access rights to our service in the settings of the Google account. In this case, your data will not be collected and processed until you have logged in to your account and given permission again.
If the user does not want to continue working with our application, he can make a request for the complete removal of the account through the Buddler technical support.
Technical security measures for the project
Security of data centers
Data centers
Buddler uses the resources of data centers in Frankfurt am Main, Germany with DigitalOcean provider.
Compliance with requirements
- The required provider compliance certificates can be found here.
- DigitalOcean is GDPR compliant. Details can be found here.
Failover protection and Redundancy
Buddler backs up user data and stores it in S3 storage. The databases conform to the standard of the primary node and several secondary nodes to which data is replicated, thus ensuring good fault tolerance.
Operational security
Data in transit
Buddler uses TLS 1.3 encryption (also called HTTPS communication protocol) throughout the site. Buddler’s HTTPS implementation uses standard algorithms and certificates.
Logging and monitoring
The data of infrastructure and business applications are logged, and critical parts of the system are also monitored. Access to logs and monitoring data is strictly limited and granted to employees based on their roles.
Patch management
Buddler regularly updates outdated packages and utilities to ensure a more current state of applications and infrastructure.
Access control
Access over the network is provided by the security rules of the provider Cloudflare, also traditional firewall rules. Access to infrastructure components and critical data is done using SSH and 2FA employee authorization.
Password policy
Buddler enforces a strong password policy across its internal systems, tools, and features. All passwords must meet defined complexity requirements and are securely encrypted. Employees must use a password manager to store their credentials safely.
Change management
Buddler implements a robust change management process to prevent unauthorized or harmful modifications to its systems and applications. All changes are thoroughly reviewed by peers, tested for functionality, and logged for auditing purposes before being rolled out to the production environment.
Privacy
Personal data storage
User personal data is deleted as soon as it is no longer needed for the specified purposes. However, we may retain copies of such data and information to the extent permitted or required by law for archival purposes or as part of automatic backups stored within standard archival systems, while ensuring the necessary technical and organizational safeguards.
Access to personal data
Personal data is protected by an appropriate level of security designed to prevent unauthorized access. Access to personal data is provided to employees based on their roles and only when necessary. The data transmission is encrypted.
Human Resources Security – Confidentiality Agreement
Our employees and contractors are required to sign a non-disclosure agreement before starting work.
GDPR
Budder products comply with GDPR requirements as of 2023/10/27. We have taken the following measures to ensure GDPR compliance:
- Collect the minimum necessary information to provide our services.
- Process data in a lawful manner.
- Maintain and provide clients with a list of subcontractors, as well as the purposes for their use.
- Enter into additional data processing agreements with our customers and suppliers that reflect the relevant security obligations of the parties and confidentiality requirements.
- Promote our services to existing and potential customers in a manner that respects their rights under the GDPR.
- Maintain a privacy policy describing our data collection practices.
We also monitor other countries’ privacy laws, such as CCPA, LGPD, and others, and comply with their requirements to ensure the security of personal data.